Fullscreen BitM: Safari Users Especially Vulnerable to Credential Stealing
Although this attack applies to all browsers, Safari users are especially vulnerable to this attack as there is no clear visual indicator of users entering fullscreen.

See How SquareX's Browser Detection and Response (BDR) Stops Fullscreen BitM Attacks
Fill out the form to request an enterprise pilot. For direct inquiries, please email founder@sqrx.com.
Fullscreen API Vulnerability
To understand why the Fullscreen BitM attack is possible, it is important to first have a good grasp of how the Fullscreen API works in browsers. By definition, the Fullscreen API allows methods to “present a specific Element (and its descendants) in fullscreen mode, and to exit fullscreen mode once it is no longer needed”.
To present an element in fullscreen mode, its requestFullscreen() needs to be called. For example, the video element elephant-video can be displayed in fullscreen with the following code:
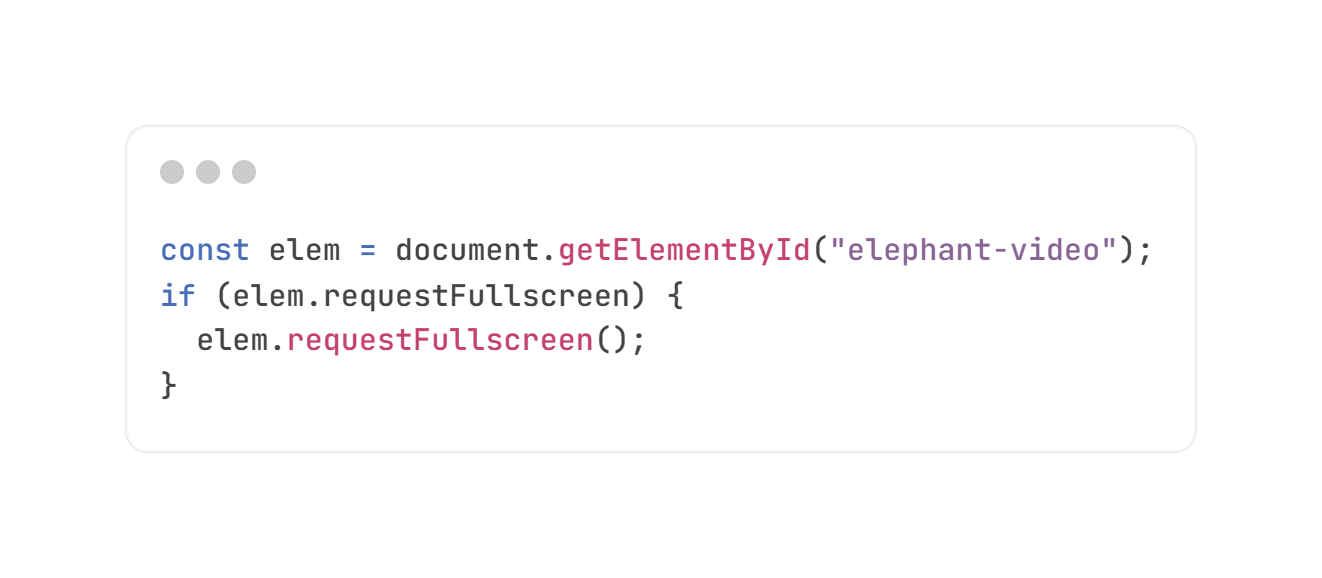
For the requestFullscreen() method to be called, browsers require a transient user activation. In other words, the user has to interact with the site or a web element on the site to activate fullscreen mode. Critically, this can be any user interaction - none of the major browsers have guardrails on the type of user interaction or web element that needs to be involved. This means that attackers can easily disguise a fullscreen button by labelling it as a sign in button or other elements that are part of the site or web application’s regular workflow.
Why is Safari particularly vulnerable to fullscreen BitM attacks?
While the attack works on all browsers, fullscreen BitM attacks are particularly convincing on Safari browsers due to the lack of clear visual cues when going fullscreen. In Firefox and Chromium-based browsers such as Chrome and Edge, there is a messaging requirement whenever fullscreen is activated. Here is an example for Chrome when expanding a YouTube video:
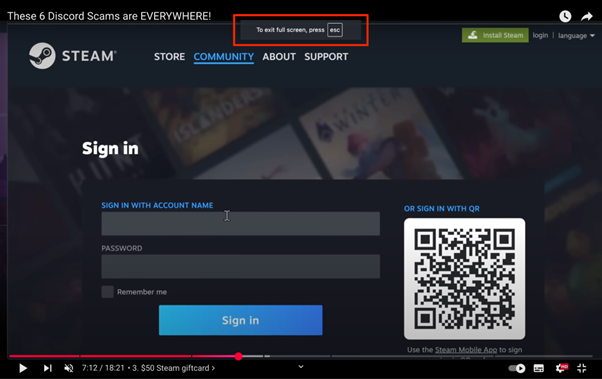
Out of the three browsers, Firefox has the clearest messaging, including details on the domain that is going fullscreen. However, this notification is subtle and transient in nature - the alert disappeared after approximately 4 seconds. Most individuals may not be security aware enough to be suspicious of fullscreens even if they see the notification. Additionally, attackers can leverage “dark modes” or color schemes similar to the warning’s color to make the pop-up less visible.


Fullscreen messaging notification for Firefox (left) and Firefox's dark mode (right)
When it comes to the Safari browser, there is no messaging requirement when the requestFullscreen() method is called. The only sign that Safari provides when entering fullscreen mode is a “swipe” animation, which is barely noticeable and more importantly, not a signal that most users associate with going fullscreen. As a result, there is practically zero visual indicator when fullscreen mode is activated in Safari browsers, a critical flaw that allows Fullscreen BitM attacks to be especially evasive in Safari browsers.
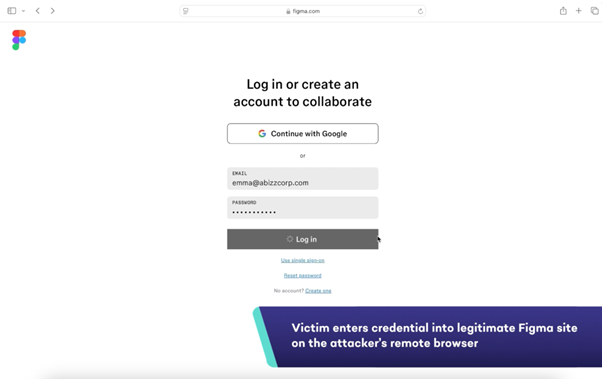
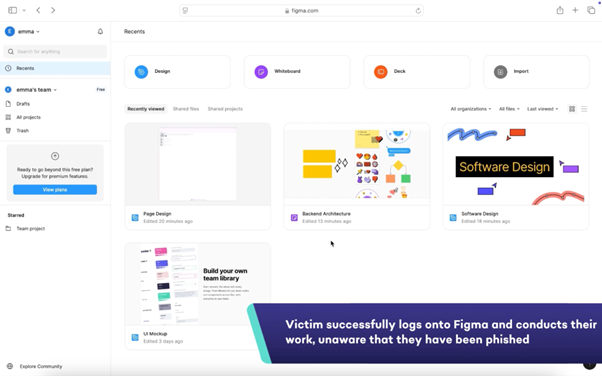
Fullscreen Browser-in-the-Middle
Note: All applications used below are for illustrative purposes, they are not more or less vulnerable to Fullscreen BitM attacks than other SaaS apps.
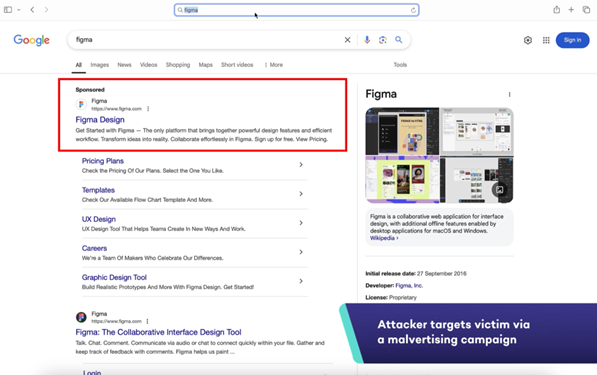
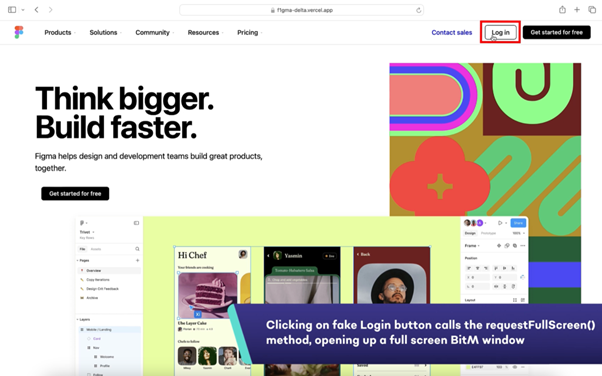
Protecting Against Fullscreen BitMs
As we see more sophisticated attacks that exploit architectural flaws in the browser, it is critical to have a browser-native solution that has full visibility into the browser to differentiate between legitimate and malicious activities. SquareX’s Browser Detection and Response (BDR) enterprise solution can protect against Fullscreen BitM attack and other client-side web attacks. As a browser extension, SquareX is a first-class browser citizen with privileges to access critical browser metrics to detect and mitigate advanced attacks on employees in the browser and is compatible across all major popular browsers.
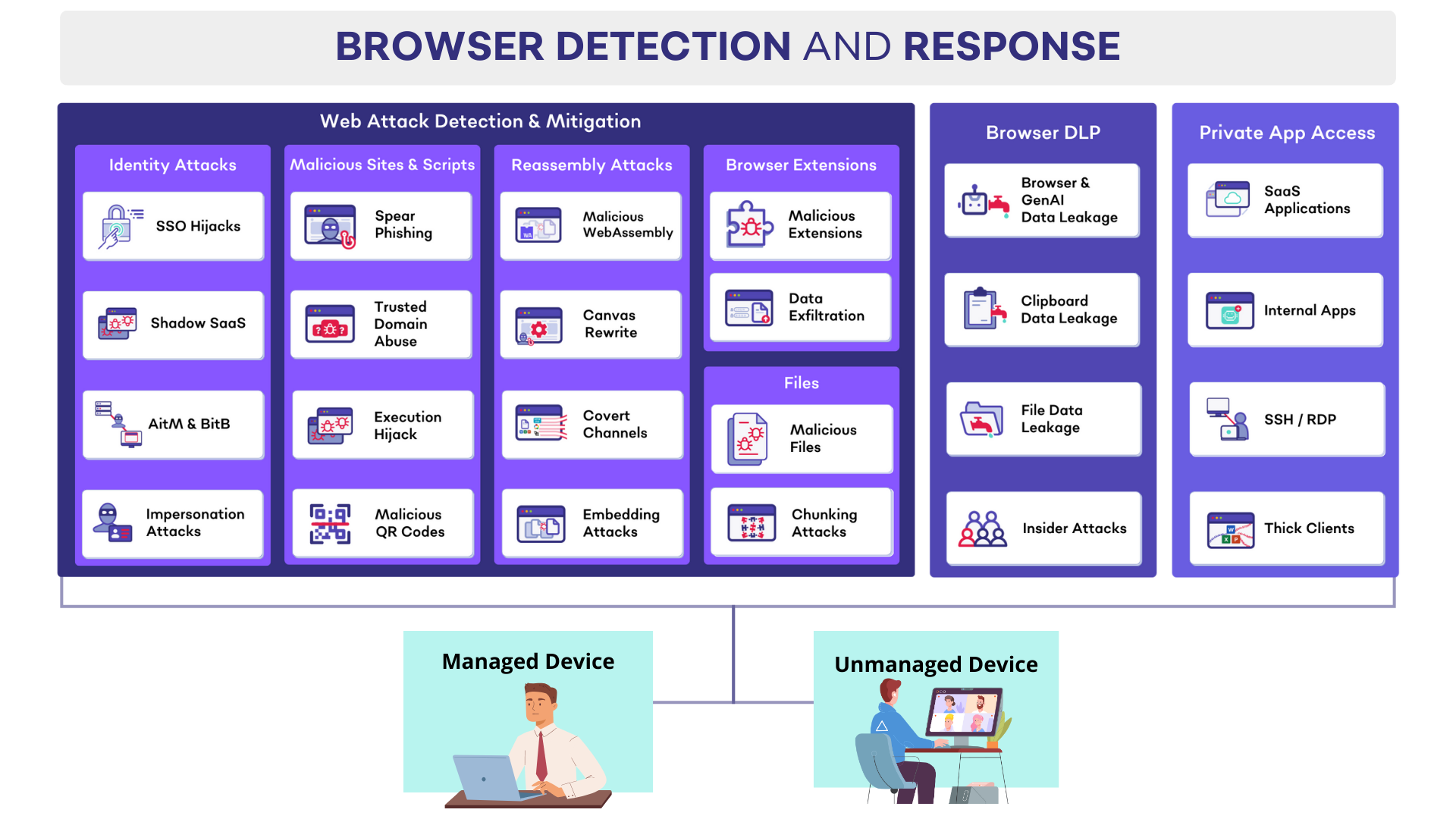
SquareX Browser Detection and Response
SquareX Browser Detection and Response SquareX’s industry-first Browser Detection and Response (BDR) solution detects, mitigates and threat-hunt client-side web attacks targeting employees in real time. There are three key components to the BDR:
- Web Threat Detection & Mitigation including identity attacks, malicious sites & scripts, malicious browser extensions and malicious files
- Browser DLP including genAI DLP, clipboard DLP, file DLP and insider attacks
- Private App Access to provide secure access to web applications and private apps via the browser, including for BYOD/unmanaged devices
The solution comes in the form of a lightweight browser extension that is compatible with all major popular browsers including Chrome, Edge, Safari and Firefox and can be easily deployed across both managed and unmanaged devices.
